So once the D5100 1.01 firmware was update was released, I couldn’t help but decrypt it.
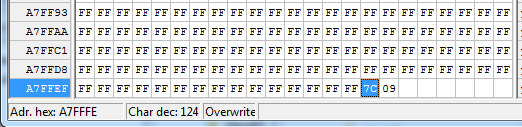
As noted in the previous post, the bundle is checksum’ed, but I didn’t mention that each sub-file is also checksum’ed. But you can see the checksum at the end of the files:
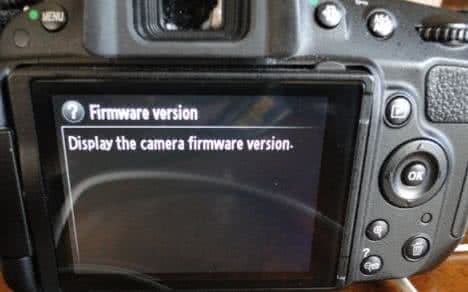
Now on some Pentax forum I was reading about people wondering if the checksum was checked. So I altered the help file text for the viewing firmware information to make the ‘c’ of camera upper case.
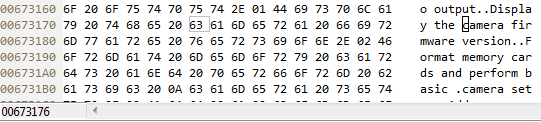
Now the file is just XOR’d with the larger one time pad discussed earlier, and ‘c’ to ‘C’ is just XOR’ing with 0x20, applying the same XOR to the encrypted file at the same location, will have the net result of making the output upper case.
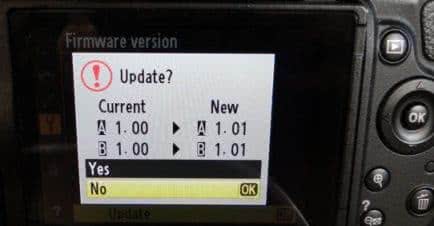
I put this altered firmware on a SD stick, and popped in into the D5100. Long story short, it recognized the update, but once I started the update, it quit really early in the process. The amount of time I’d expect for the checksum to be checked…
So I then turned to the internet for checksum algorithms, and it doesn’t appear to be a CRC-16-anything, as I brute forced the full possibility space, that was a fun adventure in multi-threading batch processing. Nor does it seam to be a Fletcher’s Checksum.
So now I’m up to searching for the answer in code…
[Update: 25 Nov] Answer found by Roos, see here
Interested in more, come join the us at Nikon Hacker, or use the Online Patch Tool (Help)
